what does "counter" mean exactly?
Counter per Wikipedia definition;
In digital logic and computing, a counter is a device that stores (and sometimes displays) the number of times a particular event or process has occurred
In CTR context; it is used to produce different inputs for the encryption, then the output is x-ored with the plaintext to produce a ciphertext. It is usually performed by incrementing, though one can use LFSR, too.
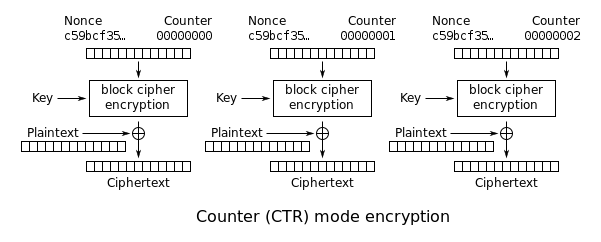
Is it the same as nonce
No, it is not the same as the nonce ( number used once)
The CTR mode combines nonce and counter, as the input to the cipher. The input is combined from two parts;
- nonce part; typically generated randomly per encryption session or by use of counter/LFSR.
- counter part; initially set zero, then incremented for every block encryption
With these we can have, randomized encryption and each block can produce a different output under the same key if we are using a PRP like AES ( PRF part is more complex and actually CTR is defined for PRFs since there is no need for the inverse)
"Typically the counter is initialized to some value and then incremented by 1 for each subsequent block (modulo $2^b$, where $b$ is the block size)". What does this statement mean exactly?
Consider that we have 64-bit nonce and 64-bit counter;
nonce counter
9237AF71A232BC82E4 0000000000000000
First block uses 9237AF71A232BC82E40000000000000000 as input, then the subsequent block uses as
nonce counter
9237AF71A232BC82E4 0000000000000001
9237AF71A232BC82E4 0000000000000002
9237AF71A232BC82E4 0000000000000003
9237AF71A232BC82E4 0000000000000004
... ...
9237AF71A232BC82E4 EFFFFFFFFFFFFFFF
9237AF71A232BC82E4 FFFFFFFFFFFFFFFF
... ...
9237AF71A232BC82E5 0000000000000000 ???
If you can encrypt $2^{64}$ blocks you will reach the end of the counter, depending on the case this can be dangerous.
If you continue from 0 counter 9237AF71A232BC82E40000000000000000 then you will have a nonce-reuse (two-time pad) issue in the CTR mode; confidentiality is lost. An observer can execute a manual crib-dragging even an automized one
If you continue increment than 9237AF71A232BC82E50000000000000000 you may hit another input that can turn into the two-time pad, too.
Stop there; actually, stop way before there if you use PRP instead of PRF.
Notes on different usages of the nonce IV term;
NIST definition uses counter as the whole input for the encryption.
Wikipedia makes a distinction. I've preferred Wikipedia's definition, In the GCM case, NIST uses IV and counter separately.
Lindell&Katz, on their book, uses IV as the $3n/4$ part of the block size and $1/4$ as for the counter. The encryption is defined as $y_i := F_k (IV || \langle i \rangle)$ They show that if the IV is uniformly selected then the IV reuse is a negligible event. Therefore CTR mode is CPA secure.






