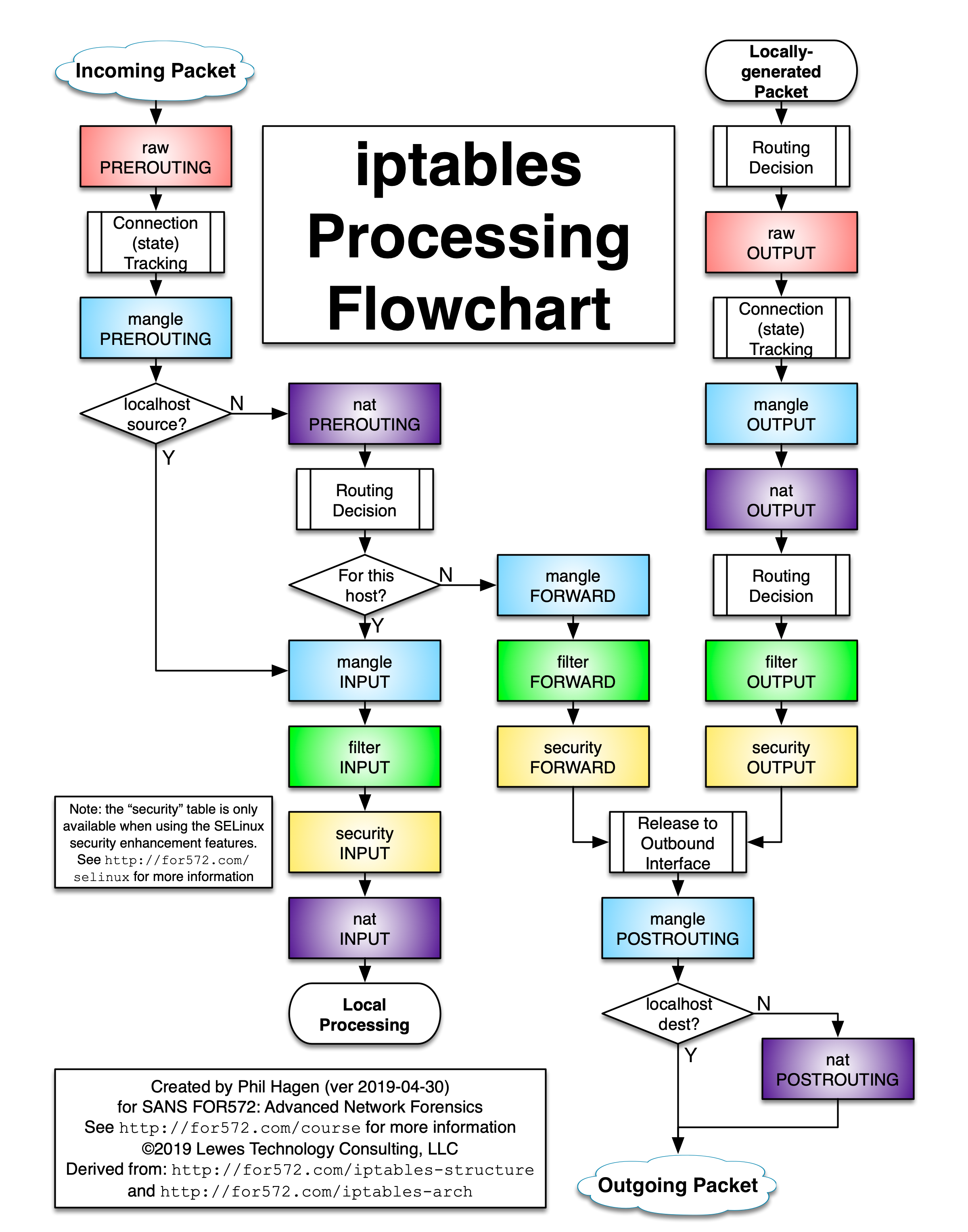
I'm running a WireGuard server on my Raspberry Pi using the https://github.com/linuxserver/docker-wireguard image. I want to allow peers to do two things:
- Connect to a single NAS via SMB
- Ping the same NAS
I've written the following iptables rules to archive this (wg0 is the WireGuard interface, eth0 the one "towards" my network):
# Reset (flush) rules
iptables -t nat -F
iptables -F
# Allow WireGuard traffic
iptables --policy INPUT ACCEPT
iptables --policy OUTPUT ACCEPT
# Deny any forward traffic by default
iptables --policy FORWARD DROP
# Allow SAMBA traffic to NAS
NAS="192.168.178.23/32"
iptables -A FORWARD -i wg0 -p tcp --dport 445 -d "$NAS" -m state --state NEW,RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -o wg0 -m state --state RELATED,ESTABLISHED -j ACCEPT
# Allow ICMP echo request
iptables -A FORWARD -i wg0 -p icmp --icmp-type 8 -d "$NAS" -m state --state NEW,RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -o wg0 -p icmp --icmp-type 0 -m state --state RELATED,ESTABLISHED -j ACCEPT
# NAT tunnel IP to internal IP
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
These work, so when connected via WireGuard I can ping and mount the NAS via SMB but I can't ping any other Service in the network or access the HTTP interface of the NAS.
I do however have a few questions to understand exactly what I've done:
- When setting
INPUT/OUTPUT policy to DROP, nothing works. My assumption is that it's because the WireGuard UDP packets received on wg0 are dropped by the policy?
- If I set the policy anyways and add a rule to
ALLOW traffic from/to wg0, the effect would be that the container can't connect to anything via eth0 and only FORWARD traffic from wg0?
- The rule allowing
RELATED,ESTABLISHED traffic via wg0 should only ever match traffic that is in response to either TCP:445 or ICMP:echo-request. No need to be more specific in there (e.g. matching port/protocol), right?
- The rule
ALLOWing echo-responses isn't needed because the less specific rule allowing RELATED,ESTABLISHED traffic above it will match before it, right?
- With all the filtering on the
FORWARD chain, my assumption is that I don't need to filter on the nat tables POSTROUTING chain, because any traffic that isn't for the NAS on either TCP:445 or ICM:echo-request won't make it "this far" anyways. Is this correct?